Nmap: A Comprehensive Guide to Network Scanning in Linux
Related Articles: Nmap: A Comprehensive Guide to Network Scanning in Linux
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Nmap: A Comprehensive Guide to Network Scanning in Linux. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Nmap: A Comprehensive Guide to Network Scanning in Linux
![Linux nmap command (network scan) [Basic Guide] - Linux Certification](https://www.linuxcertification.academy/wp-content/uploads/2022/11/Scan-your-network-with-nmap.jpg)
Nmap, short for Network Mapper, is an indispensable tool for network administrators, security professionals, and anyone interested in understanding the structure and security posture of a network. It is a powerful, open-source network scanner that allows users to discover hosts, identify open ports, determine operating systems, and gather other valuable network information. Nmap’s versatility and comprehensive feature set have solidified its position as a cornerstone of network exploration and security analysis.
Understanding the Core Functionality of Nmap
At its core, Nmap operates by sending specially crafted packets to target hosts and analyzing the responses. These packets can be tailored to elicit specific information, allowing Nmap to perform a wide range of tasks, including:
- Host Discovery: Nmap can identify active hosts on a network by sending out "ping" requests and analyzing the responses. This process helps map out the network topology and pinpoint devices that are online.
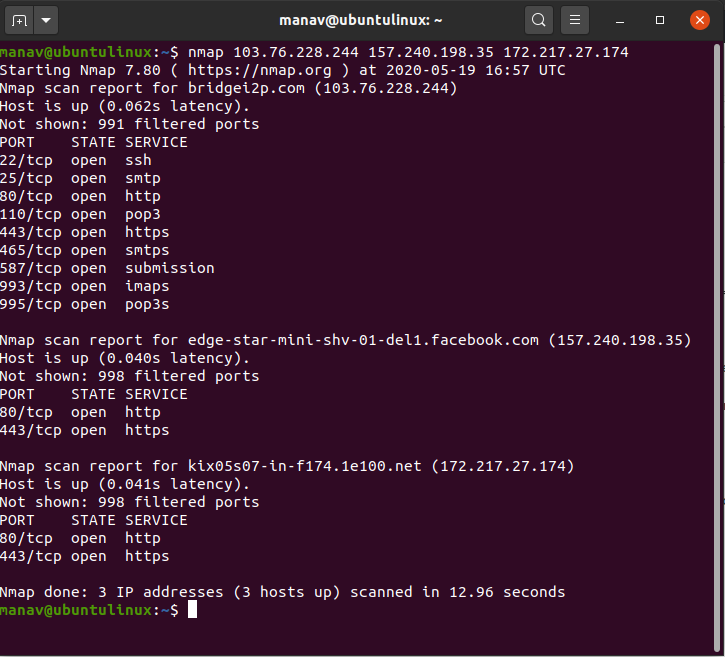
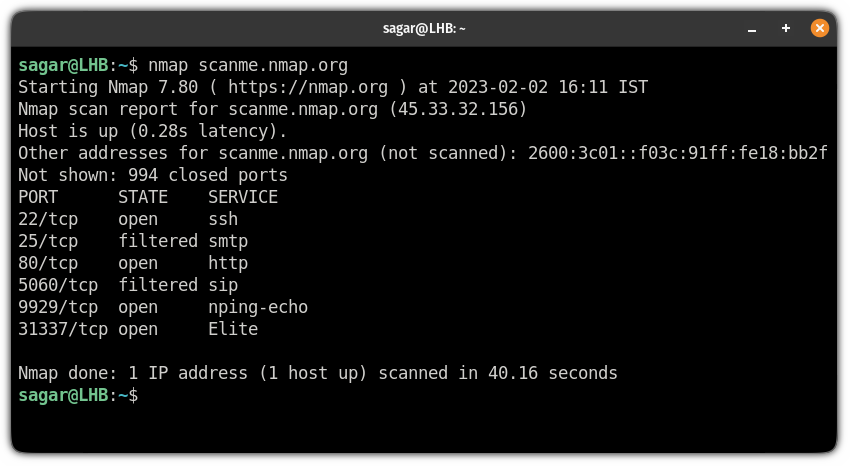
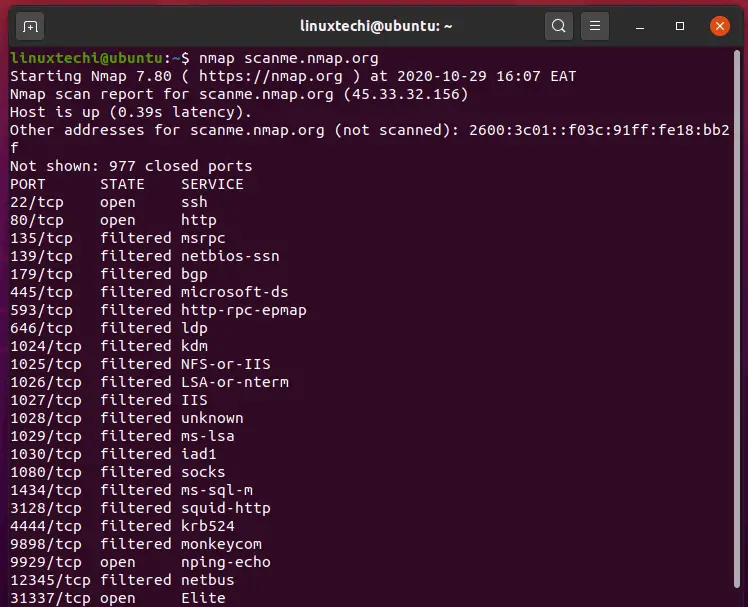
- Port Scanning: Nmap can probe specific ports on a host to determine which ones are open and potentially listening for connections. This information is crucial for understanding the services running on a host and identifying potential vulnerabilities.
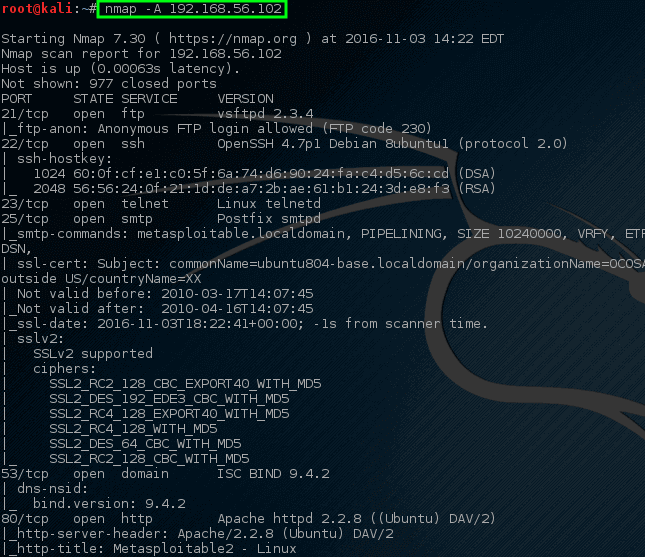
- Operating System Detection: By analyzing the responses to specific packets, Nmap can often deduce the operating system running on a target host. This information can be valuable for identifying potential security risks and tailoring attack strategies.
- Service Version Detection: Nmap can go beyond simply identifying open ports and determine the version of the service running on that port. This provides crucial information about potential vulnerabilities and outdated software that could be exploited.
- Network Mapping: Nmap can be used to create detailed maps of a network, showcasing the connections between devices, the services running on each host, and the overall network topology.
Nmap’s Diverse Scanning Techniques
Nmap offers a variety of scanning techniques that allow users to tailor their scans to specific needs and security contexts. Some of the most commonly used techniques include:
- TCP Connect Scan: This is the most basic and straightforward scanning technique. Nmap attempts to establish a full TCP connection to each target port. This method is reliable but can be easily detected by firewalls and intrusion detection systems.
- SYN Scan (Half-Open Scan): This technique sends a SYN packet to each target port and waits for a SYN/ACK response. This method is less intrusive than the TCP Connect scan and is harder to detect, making it a popular choice for stealthy scans.
- UDP Scan: Nmap can also scan UDP ports by sending UDP packets and analyzing the responses. This method is less reliable than TCP scans due to the nature of UDP, but it can be useful for identifying UDP-based services.
- FIN Scan: This technique sends a FIN packet to each target port and observes the response. This method is more stealthy than TCP Connect scans and can sometimes bypass firewalls.
- NULL Scan: This technique sends a packet with all flag bits set to zero. This method can be useful for bypassing firewalls that block SYN packets.
Beyond Basic Scanning: Advanced Nmap Features
Nmap’s capabilities extend far beyond basic scanning. The tool offers a wide range of advanced features that provide valuable insights and enhance security analysis:
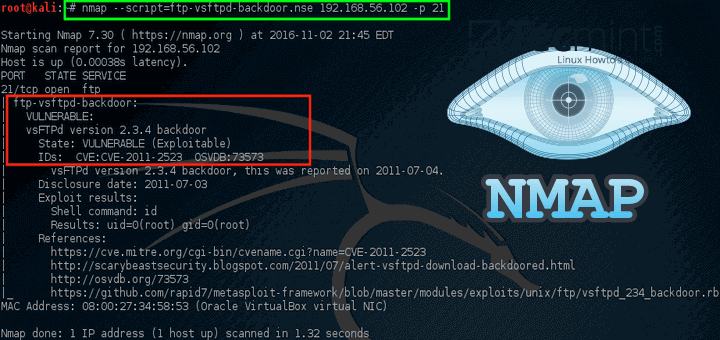
- Script Scanning: Nmap allows users to execute custom scripts against target hosts. These scripts can perform various tasks, including vulnerability scanning, service detection, and even brute-force password attacks.
- OS Fingerprinting: Nmap’s OS fingerprinting capabilities allow it to identify the operating system running on a target host with high accuracy. This information can be crucial for security assessments and targeted attacks.
- Service Version Detection: Nmap can detect the version of a running service on a target host, enabling users to identify potential vulnerabilities and outdated software that could be exploited.
- Network Mapping and Visualization: Nmap can generate detailed maps of a network, showcasing the connections between devices, the services running on each host, and the overall network topology. These maps can be visualized in various formats, providing a comprehensive overview of the network structure.
- Customizability and Extensibility: Nmap is highly customizable and extensible, allowing users to tailor the tool to their specific needs. Users can create custom scripts, modify scan parameters, and even develop their own Nmap plugins.
Practical Applications of Nmap
Nmap’s versatility and comprehensive feature set make it an invaluable tool for various tasks, including:
- Network Security Auditing: Nmap is extensively used for security audits, identifying open ports, vulnerable services, and potential attack vectors. It helps security professionals assess the overall security posture of a network and identify areas for improvement.
- Vulnerability Scanning: Nmap can be used to scan for known vulnerabilities in systems and applications. By combining Nmap with vulnerability databases and custom scripts, security professionals can quickly identify exploitable weaknesses and take appropriate mitigation steps.
- Network Discovery and Mapping: Nmap’s network mapping capabilities allow administrators to gain a clear understanding of the network topology, identify connected devices, and troubleshoot network issues.
- Service Discovery and Inventory Management: Nmap helps administrators identify running services, track software versions, and manage network resources effectively.
- Penetration Testing: Nmap is a critical tool for penetration testers, allowing them to identify potential attack vectors, test security controls, and simulate real-world attacks.
FAQs about Nmap
Q: Is Nmap legal to use?
A: Nmap itself is a legal tool. However, using it to scan networks without permission can be illegal. It is essential to respect network security policies and obtain consent before scanning any network.
Q: Is Nmap safe to use?
A: Nmap is a powerful tool, and its misuse can lead to unintended consequences. It is important to understand the potential impact of your scans and use Nmap responsibly.
Q: Can Nmap be used for malicious purposes?
A: Like any tool, Nmap can be used for malicious purposes. However, Nmap is primarily designed for legitimate network analysis and security testing.
Q: How can I learn more about Nmap?
A: Nmap’s official website provides comprehensive documentation, tutorials, and resources. The Nmap community is also active and helpful, offering support through forums and mailing lists.
Tips for Using Nmap Effectively
- Start with Basic Scans: Begin with simple scans to understand the network structure and identify active hosts.
- Use Stealthy Techniques: Employ stealthy scanning techniques like SYN scans to minimize detection by firewalls and intrusion detection systems.
- Customize Scans: Tailor your scans to specific needs by adjusting scan parameters, using custom scripts, and exploiting Nmap’s extensive features.
- Analyze Results Carefully: Pay close attention to scan results and interpret them accurately to identify potential security vulnerabilities and network issues.
- Respect Network Security Policies: Always obtain permission before scanning a network and adhere to network security policies.
Conclusion
Nmap is a powerful, versatile, and indispensable tool for network administrators, security professionals, and anyone interested in understanding the structure and security posture of a network. Its comprehensive feature set, advanced scanning techniques, and robust scripting capabilities make it a cornerstone of network exploration and security analysis. By mastering Nmap’s capabilities, users can gain valuable insights into network infrastructure, identify potential vulnerabilities, and enhance their overall security posture.



Closure
Thus, we hope this article has provided valuable insights into Nmap: A Comprehensive Guide to Network Scanning in Linux. We thank you for taking the time to read this article. See you in our next article!